Context-Aware Security Intelligence of Vulnerability Scanners in Cloud-native environments
How do you scan multiple applications for security issues while filtering out false alarms? Automate that process with contextual information like your application’s topology — an approach based on my master’s thesis with Dynatrace.

In the ever-changing cybersecurity landscape, having accurate and current information at your disposal is more critical than ever. If you’re a security expert, you have dozens of web applications that you need to scan regularly for vulnerabilities. Scanning all these apps can be daunting, especially considering the time required to analyze the results and filter out false alarms. That’s where my master’s thesis project Themis comes in.
Themis automates the process of vulnerability scanning and filtering the findings by using contextual information like the topology of your applications, so you can focus your time and resources on fixing the identified issues.
This blog post is a follow-up to the paper: Context-Aware Security Intelligence of Vulnerability Scanners in Cloud-native Environments.
Introducing the approach behind Themis
Themis proposes a technique to reduce false positives of security tools in a cloud-native environment by utilizing contextual information, especially topology, runtime, and attack information, visualized in the following figure. The proposed method is generally applicable, but Themis mainly focuses on the open source web application security scanner OWASP ZAP and relies on Dynatrace, with the power of Grail, to collect all the necessary contextual information from your applications. (Other scanners besides OWASP ZAP could be added in the future if the proper transformers are developed.)
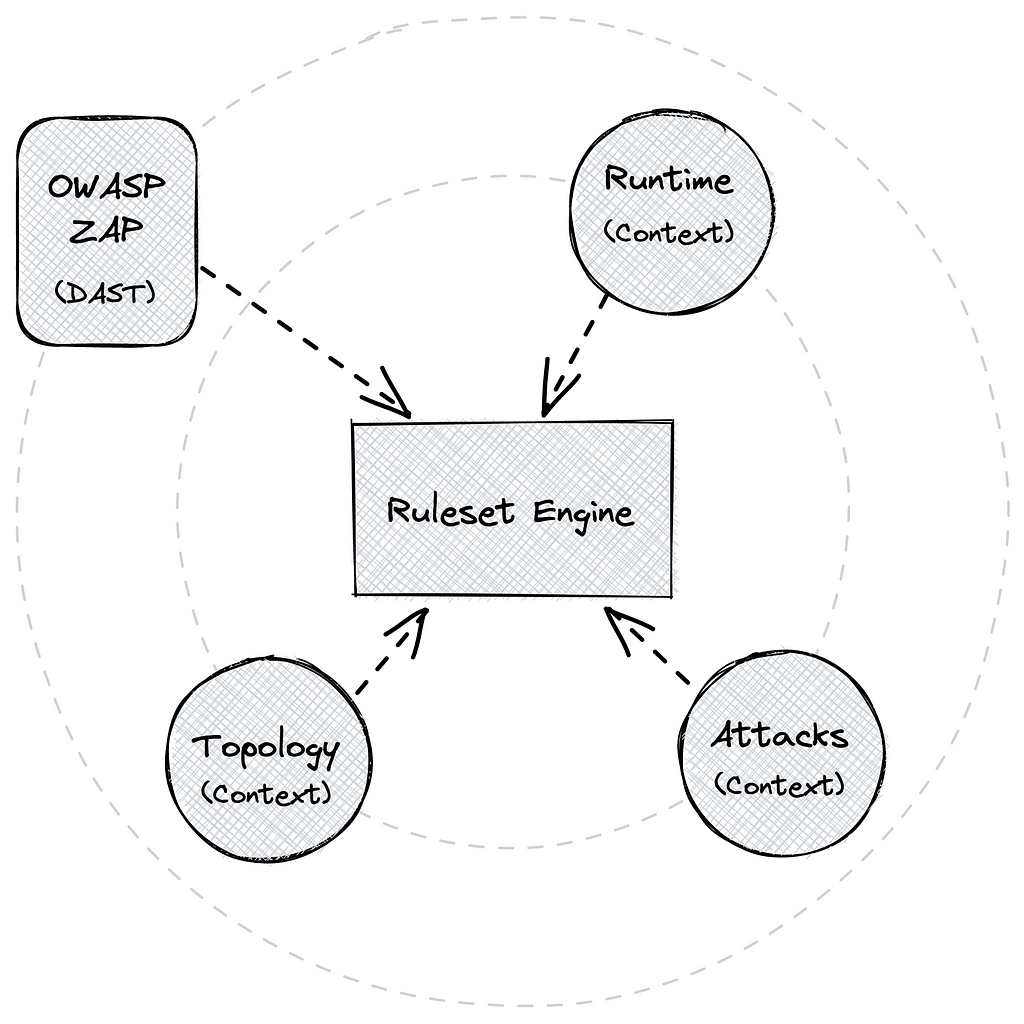
The core features of Themis are:
- Graph-based security posture visualization: Themis visualizes the relationship between application assets from an attacker’s perspective to assist security experts in mitigation.
- Context-aware ruleset engine: Dynamic Application Security Testing (DAST) scanners are known to report false-positive alerts. A filtering mechanism with user-defined rules based on contextual topology information filters specific security findings and reduces the false-positive ratio.
How does it work, and what are its benefits?
Behind the scenes, Themis consists of four main components that, in turn, consist of one or more sub-components, as the following figure shows.
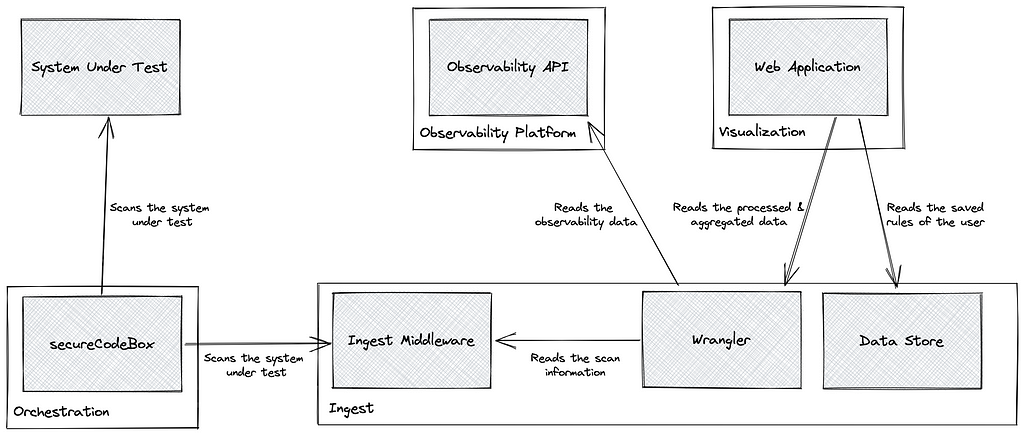
Observability Platform
The Dynatrace platform offers constant insight into the services and collects monitored data. The following listing shows how this would be captured in an exemplary JSON object used by Themis. It contains information about each entity’s OS or SDKs and spans, a unit of work in a trace used to reconstruct topology changes and detected attacks based on the Dynatrace real-time attack protection data.
"entities": [
"type": "string",
"osName": "string",
"sdk": {
...
}
],
"spans": [
"spanId": "string",
"kind": "string",
"parentId": "string",
"entityId": "string",
"http": {
"host": "string"
}
],
"attacks": [
"type": "string",
"state": "string",
"target": {
...
},
"affectedEntities": {
...
}
]
Orchestration
The orchestration uses the open source secureCodeBox project to run OWASP ZAP scans against multiple applications and extract the results to a unified format relayed to the ingest component.
Ingest
The core part of this work, the ingest, is split into three parts:
- The Ingest Middleware transforms the result of the orchestration component and potential external vulnerability scanners into a unified DAST report format.
- The Wrangler then uses this report to combine the results with the data of the observability platform. The combination is performed based on the hostname of the application, which is present in the span data and the scan result.
- The aggregated data should be able to filter scan results with pre-and user-defined rules, which are saved in the datastore.
Visualization
The visualization of Themis is an app built using the new Dynatrace® AppEngine that allows security experts to view the ingest security findings and configure rules to filter false positives.
How do you use Themis to improve your scan results?
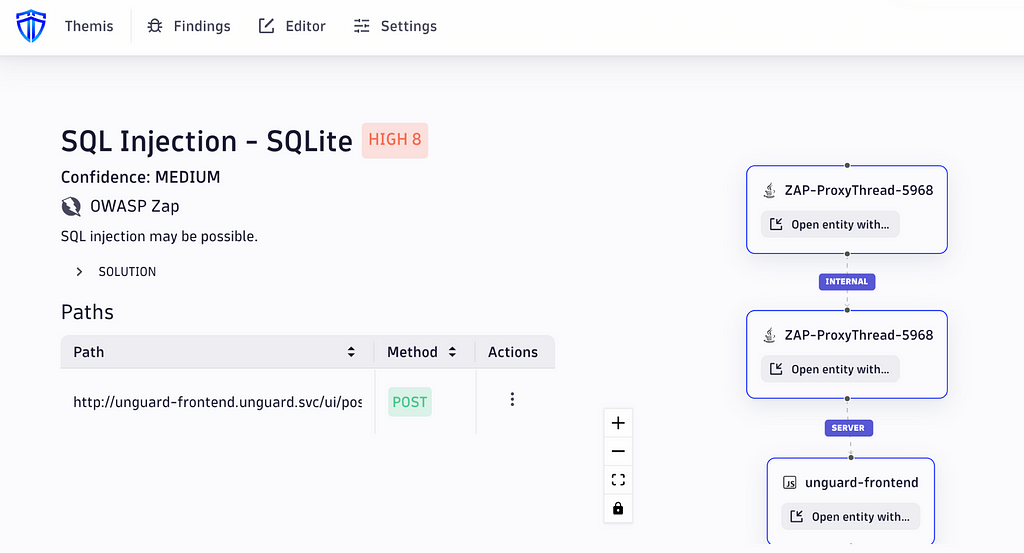
When opening Themis, you’ll be presented with a list of all the collected security findings of your web vulnerability scanners. You can select a result to open an additional page containing more information, for example, the confidence level and possible solutions, if any exist. On the same page, you’ll see the graph-based visualization of the traces that assists users in understanding what kind of network traffic a finding generated.
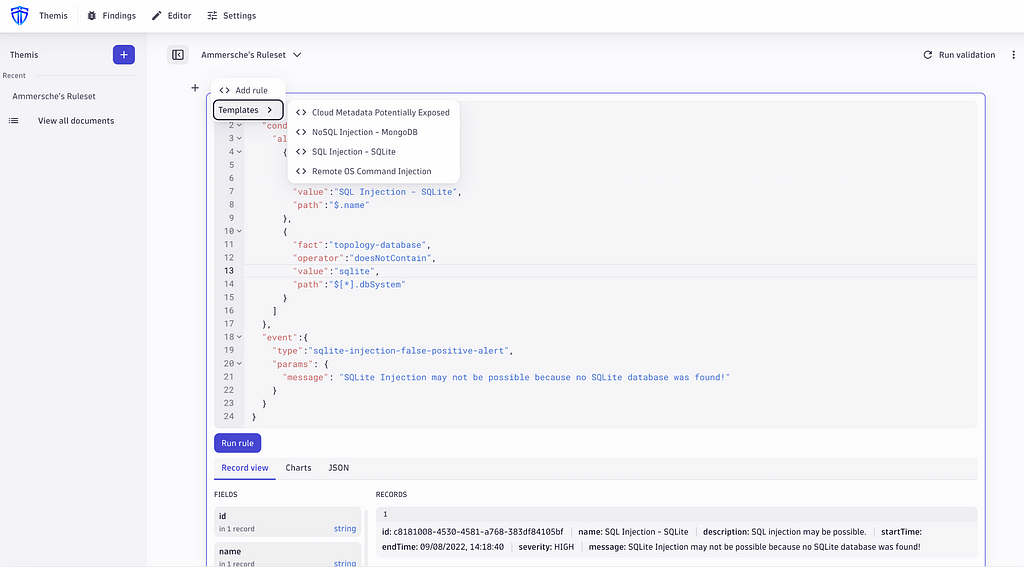
The Themis editor enables security experts to create rulesets, as shown in the left navigation bar. Each ruleset consists of multiple rules that can be added by clicking the button with the plus icon. Themis already provides rules for four vulnerability scenarios as templates.
{
"conditions":{
"all":[
{
"fact":"finding",
"operator":"equal",
"value":"Cloud Metadata Potentially Exposed",
"path":"$.name"
},
{
"fact":"topology-http-server",
"operator":"doesNotContain",
"value":"nginx",
"path":"$[*].httpServerName"
}
]
},
"event":{
"type":"cloud-metadata-potentially-exposed-false-positive-alert",
"params": {
"message": "Cloud Metadata Potentially Exposed may not be possible because no Nginx HTTP server was found!"
}
}
},
{
"conditions":{
"all":[
{
"fact":"finding",
"operator":"equal",
"value":"NoSQL Injection - MongoDB",
"path":"$.name"
},
{
"fact":"topology-database",
"operator":"doesNotContain",
"value":"mongodb",
"path":"$[*].dbSystem"
}
]
},
"event":{
"type":"nosql-injection-mongodb-false-positive-alert",
"params": {
"message": "NoSQL Injection may not be possible because no MongoDb database was found!"
}
}
},
{
"conditions":{
"all":[
{
"fact":"finding",
"operator":"equal",
"value":"SQL Injection - SQLite",
"path":"$.name"
},
{
"fact":"topology-database",
"operator":"doesNotContain",
"value":"sqlite",
"path":"$[*].dbSystem"
}
]
},
"event":{
"type":"sqlite-injection-false-positive-alert",
"params": {
"message": "SQLite Injection may not be possible because no SQLite database was found!"
}
}
},
{
"conditions":{
"all":[
{
"fact":"finding",
"operator":"equal",
"value":"Remote OS Command Injection",
"path":"$.name"
},
{
"fact":"attack",
"operator":"lessThanInclusive",
"value":"0",
"path":"$.totalCount",
"params":{
"attackType":"COMMAND_INJECTION"
}
}
]
},
"event":{
"type":"remote-os-command-injection-false-positive-alert",
"params": {
"message": "Remote OS Command Injection may not be possible because no attack was found (only Java supported at the moment)!"
}
}
}The following figure shows a rule for an SQL injection in the SQLite vulnerability that checks whether applications with this reported finding use an SQLite database. Each rule can also be evaluated by clicking the ‘Run rule’ button. If a matching rule is found, it is shown as a record beneath it.
Final thoughts
The proposed architecture and Themis prototype show positive preliminary results in reducing false positives for security tools in a cloud-native environment. Although more research is needed to explore the potential of this approach further, it shows promising results for improving the accuracy of web application scanners.
We encourage you to contact us if you’re interested in exploring this technique further.
Context-Aware Security Intelligence of Vulnerability Scanners in Cloud-native environments was originally published in Dynatrace Engineering on Medium, where people are continuing the conversation by highlighting and responding to this story.
